Decrypt Keychain.plist
Explanation of the hash formatIf the backup was generated by iOS version less than 10, the hash will look like:$itunesbackup$.9.b8e3f3a970239b22ac199b622293fe4237b9d16e74bad2c3c3568cd1bd3c471615a6c4f86720.If the backup was generated by iOS version 10.x, the hash will look like:$itunesbackup$.10.8b715f516ff8e64442c478c2d9abb046fc6979ab079007d3dbcef3ddd84217f4c3db01362d88fa68.30000.425b4bb4e200b5fd4c66979c9caca3. Manifest.plist contentBinary plist with the following content (dict):. Applications (dict):. com.apple.iBooks (dict).
CFBundleIdentifier (string): com.apple.iBooks. CFBundleVersion (string): 804. Path (string): /private/var/mobile/Applications/GUID/iBooks.app. etc.
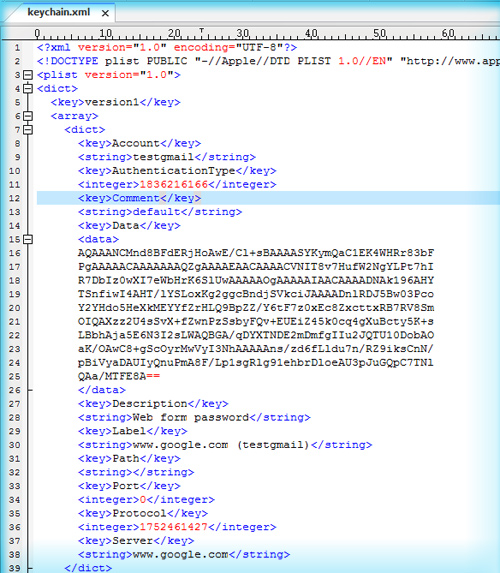
Plist Editor Pro for Windows - A software for reading and edit plist files. What is plist Editor Pro? In the Mac OS X and iPhone OS, property list files are files that store serialized objects. Property list files use the filename extension.plist. Mac OS X 10.2 introduced a new format where property list files are stored as binary files. When using CryptProtectData, Safari uses a standard, static salt for all passwords which is also stored in the keychain.plist file. So to actually decode the XML file, you must first decrypt the BASE64 encrypted data, then decrypt the Windows DPAPI encrypted data.
Would you nonchalantly walk down the street holding $600 cash in your hand? Would you forget that same wad of cash on a restaurant table after dinner?Unless you’re very rich or very foolish, you probably are going to be very conscious of a $600 wad of cash.How about your $600 iPhone or Android? Most people don’t think of their phone in the same context as a wad of cash, but that’s exactly what it is. The following are some common sense tips to keeping your phone in hand (or pocket).What to do before you lose your device:. Password protect your phone! Yes it’s a bit frustrating to have to enter a pin every time you want to access your phone – consider it paying your insurance premium. If you store any sort of personal information, people’s contact information (including e-mail addresses), directions to your house, favorite stores, etc.
Or any other personal information – don’t make it any easier than you have to for a thief to get access to your information. Last but not least, don’t!
Make it something easy like “1234” or your birthday!. Use remote protection apps such as BlackBerry Protect from BlackBerry App World, “Find My iPhone”, or “Prey” for Android – these apps can either help you find or wipe phone your phone remotely.
Make a record of your phone ESN, IMEI or MEID number – usually found under the battery cover, this will make it much easier to report the lost/stolen phone to your carrier or the police. Backup your data on regular basis! I recommend backing up your phone to your computer at least once a month if not once a week.
If you use a service such as gmail for storing your contacts, they are already backed up – but don’t forget your pictures, or any other files you may store on your device!. Finally, be careful how you use and store your phone. Be aware of your surroundings, don’t leave your device in plain sight in a vehicle or public space.
Be careful about displaying headsets and ear-buds while in public. White iPhone ear-buds are equivalent to posting a “I have $600 cash in my pocket” sign on your back.What to do after you lose your device:. Send text to phone & call it – if it’s lost, someone may find it & return it to you. If it’s stolen – this probably won’t help much. Try using the remote locator application that you (hopefully) installed. You might be able to find your device or track it as someone moves around with it. If your sure your phone is gone, use the remote wipe application that you (hopefully) installed.
Most thieves don’t care about your data – they just want to turn your device into cash, but why take a chance?. Contact security or authorities – it’s possible that your device might have been found or put in lost & found.
Call carrier & report lost/stolen phone – ask to suspend your service (messaging & calls) so thieves won’t be able to use it for expensive international calls. How many times have you heard about a celebrity, politician or even friends and family who have their e-mail accounts hacked? Ever had an Excel file that grows to tremendous size and takes forever to load? Or seemingly triples in size overnight?Here are a few tips and tricks we will cover to identify what’s causing Excel file size bloat:.
Convert file format from.XLS to.XLSX. Delete Pivot Table saved data. Remove unnecessary cell formatting.
Determine if file contains corrupted dataNote: The tips & tricks discussed here are written for Excel 2010. Most of them will also work in other versions of Excel but may require some modification to the instructions.VERY IMPORTANT! Before modifying your files, make a backup copy in case you break something!1. Convert File FormatPre-Excel 2007, there was only one file format for Excel files,.XLS.
With the advent of Excel 2007 and beyond, there is a new file format,.XLSX which is able to store more data in a smaller file. You can easily convert an old, XLS file into the new format by:.
Open the file. Select the “File” tab on the Ribbon. Select “Save As” from the options. In the “Save as type:” drop box select “Excel Workbook (.xlsx)”. Select the “Save” button2.
Non of this wouldn’t even be possiblewithout every single one of our dedicated fans who helped us with the purchase of many games in the development process.For this we are grateful and here we present the complete steam key generator or keygen for short to everyone thatenjoys the steam games, but doesn’t have the funds to get all of them. Steam cd key generator download. That’s not all though, we do not simply generate the keys like other tools show you as well but we also take the extra step to redeem them on Steam to prove to you that they are actually working keys.We spend numerous hours reasearching the steam algorithms and developing our keygen. Try out the game with our keygen and thinkof purchasing it afterwards to support the developers.
Delete Pivot Table Saved DataBy default, pivot tables store their calculated data in the file. You can turn off this functionality and delete and stored data to free up space and compress the file size.To delete pivot table stored data:. Right-click on a pivot table and select “PivotTable Options ”. Select the “Data” tab. In the “PivotTable Data” section, uncheck the “Save source data with file” check box.
Select the “Refresh data when opening the file” check box. In the “Retain items deleted from the data source” section, in the “Number of items to retain per field” drop box, select “None”.
Select the “OK” button to save your changes.3. Remove Unnecessary FormattingEverything you do to an Excel file increases it’s size.
This includes not just the data entered into a cell but also the cell formatting. Making a column bold or highlighted green etc.To help reduce file size, remove any cell formatting that is not required. Common occurrences of unnecessary cell formatting include:. Formatting on any tabs that are used for calculations but are not required to be viewed by the end user. Applying grid lines or white “fill” to all cells in a worksheet. Only apply formatting to cells which are actually being used or printed.4. Corrupt DataAny file on a computer can become corrupted due to many different factors.
Excel files can not only become corrupted as a whole, but individual tabs within your worksheet can also become corrupted. The file may open and you may not even notice anything odd on your worksheet but the size of your file may skyrocket from a couple hundred kilobytes to hundreds of megabytes! It can be very difficult to figure out where the data in the file is corrupted but here are a couple of tricks to determine where the corruption is as well as how to potentially fix it. On each sheet, go up to the very first cell, A1 and press the Ctrl+End key combo. This will cause your cell selection to jump to the bottom-most cell where Excel believes it has data.
If a file is corrupted, many times this will cause your cell selection to jump down hundreds or even thousands or lines below where your data is. In fact, you will probably be selecting a completely blank cell in a sea of blank cells. If this occurs, try deleting all rows and all columns that do not contain data in the sheet.
Save your file and see if your file size is reduced. Do this for all sheets in your file.
Another option to find corrupt data, is save your file as an HTML file. When Excel exports your data into HTML, it will create a new HTML document for each worksheet. You can then view the size of each HTML document to get a rough feel for which sheet is probably corrupt.To export your file as HTML:. Select “File” from the ribbon menu. Select “Save As” from the menu.
In the “Save as type:” drop box select “Web Page (.htm;.html)”. Select the “Save” buttonOnce you have saved the file as HTML, open up the folder where you saved it and check the file sizes. The HTML files are named with the back-end worksheet names used in the VBA editor. The other day, a co-worker of mine called me and asked for help with a spreadsheet. He had a number of calculations and when he got to the end of them the number looked wrong so he calculated the number manually on a calculator and got a different answer!Turns out, he did not realize that by default, Excel rounds calculations and only displays the number of decimals that you specify (defaults to 2 decimals when formated as a number). It took me a while to understand what he was talking about too because I came at it from the other direction, I never though that Excel would only calculate to the precision of the displayed value!There is actually a buried setting that will make Excel calculate cells with as much precision as the displayed format.
To enable/disable this option, go to File Options Advanced When calculating this workbook: “Set precision as displayed”.However, there are dangers to using this setting and I want to make sure they are clear before you go enabling it. I think it’s safe to assume that most people do not use (or even know) about this option.
As such, most people work with Excel expecting it to round cell values visually but not round the actual background calculations. A while ago I posted a how to video on YouTube as an experiment and then forgot all about it.I have decided to post it here to the blog and see if people like it. One piece of feedback I have received is that people wanted to hear me talking. My thought was, if I was watching this video, I would probably be in an office setting and not want to interrupt others with sound – hence, subtitles and no voice. Have an opinion?
Want to hear my voice? Leave a comment and let me know!Thanks and enjoy!Yosef. Part 1 of this series may be found.Part 2 of this series may be found.Part 3 of this series may be found.Part 4 of this series may be found.SafariI must admit, I was pretty surprised by how hidden Apple made their security information. After years of hearing how horrible Safari is in terms of general security – their password security is actually pretty decent. Part 1 of this series may be found.Part 2 of this series may be found.FirefoxFirefox by default has lousy security. However, if you enable the Master Password option (off by default), Firefox has the most secure security go figure.Firefox stores usernames and passwords in a SQLite database called signons.sqlite which can be found in the following folders:Windows XP:C:Documents and SettingsusernameApplication DataMozillaFirefoxProfilesrandomname.defaultWindows Vista7:C:UsersusernameAppDataRoamingMozillaFirefoxProfilesrandomname.defaultIn the SQLite database, the username and password are encrypted using Triple DES and BASE64 encryption algorithms. The decryption hash is stored in a file called key3.db in the same folder structure.
By default, if a master password is not set, Firefox will allow any user to open up the signons.sqlite and key3.db files to view the usernames and passwords directly in the browser, no questions asked. As long as someone has a copy of the two files, they can transfer them to any machine and view the data.However, if the Master Password is set, then Firefox will store a one way hash in the key3.db file and require you to input the password to generate a matching hash in order to decrypt the signons.sqlite database. Without the Master Password, no one can decrypt the data.
Therefore, your data is as secure as your Master Password. Without it, there’s virtually no security on your data.